I don’t know if I should be laughing about this news or if I should pity the report about what happened to our country’s second in command – Vice-President JEJOMAR “JOJO” C. BINAY’ official website yesterday, Sunday (New Year’s day). The official website of VP Binay was defaced by a group of hackers known PrivateX and along with this was the Philippine Nuclear Research Institute (PNRI). For those who doesn’t know or doesn’t have any idea about the word “defaced” or “defacing”, it is the word used by hackers that simply means altering someone’s website and usually they don’t delete the whole www directories but only changing or renaming the original initial page or index and putting the hacker’s own customized index page. Normally, this kind of act is used by white hackers to show the owner or administrator of the target website that they are not secured and should do the necessary actions to tighten the security of their website. While others such as the Black hackers will probably plant a bomb on the targeted website and delete the whole thing – ouch!
Anyway, the attack on Vice President’s official website was made yesterday evening before 9PM by the group of hackers called PrivateX. And it looks like that the original website was already restored by the web administrator. However, based on the description while on its defaced state it has an embedded video report with Joey Salgado whom denies that the website was never been hacked before (well, this probably provoked the hackers). Also, the OVP’s website was just recently transferred to a paid web hosting – looks like pregi.net.
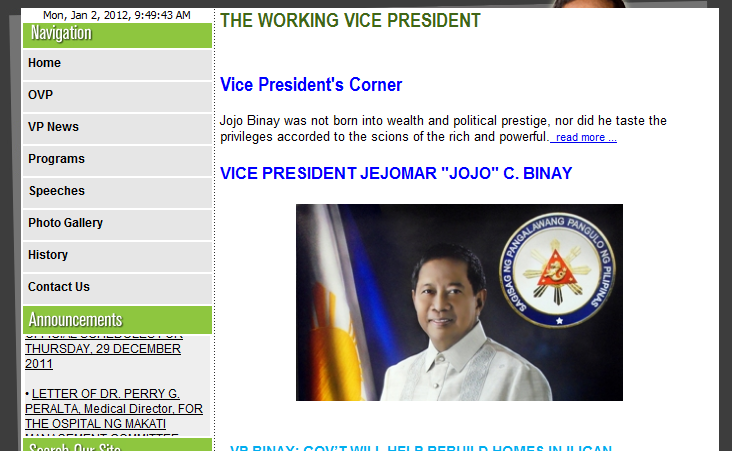
However, according to PrivateX on their official Facebook fan page, they clarified the “purpose” of the embedded video on the defaced website of OVP was not meant to taunt the Administration of the Vice-President but to highlight or emphasized that transferring one’s website or domain to a paid web hosting does not mean that your website is already secured. They also said that they did not delete any files but rather added an index.html and redirected the index.php to the added index.html which was the defaced page.
This is actually not new to me and to be honest I already tried this sometime during my college days and even when I was already working (just on my first year at work) since I was made part of the RnD group in an ISP which requires me to exploit our own websites before just to check if it is fully secured. We have scripts before to do it and mostly the affected servers are those with un-updated IIS web servers. But I think the method and approach have already changed and evolved since then – poor me I guess. But although I feel for those who have been attacked and defaced, this should still serve as a wake up call for them to call the attention of their administrators to do their job in making sure that they have tightened the security – especially if it is a paid web hosting.